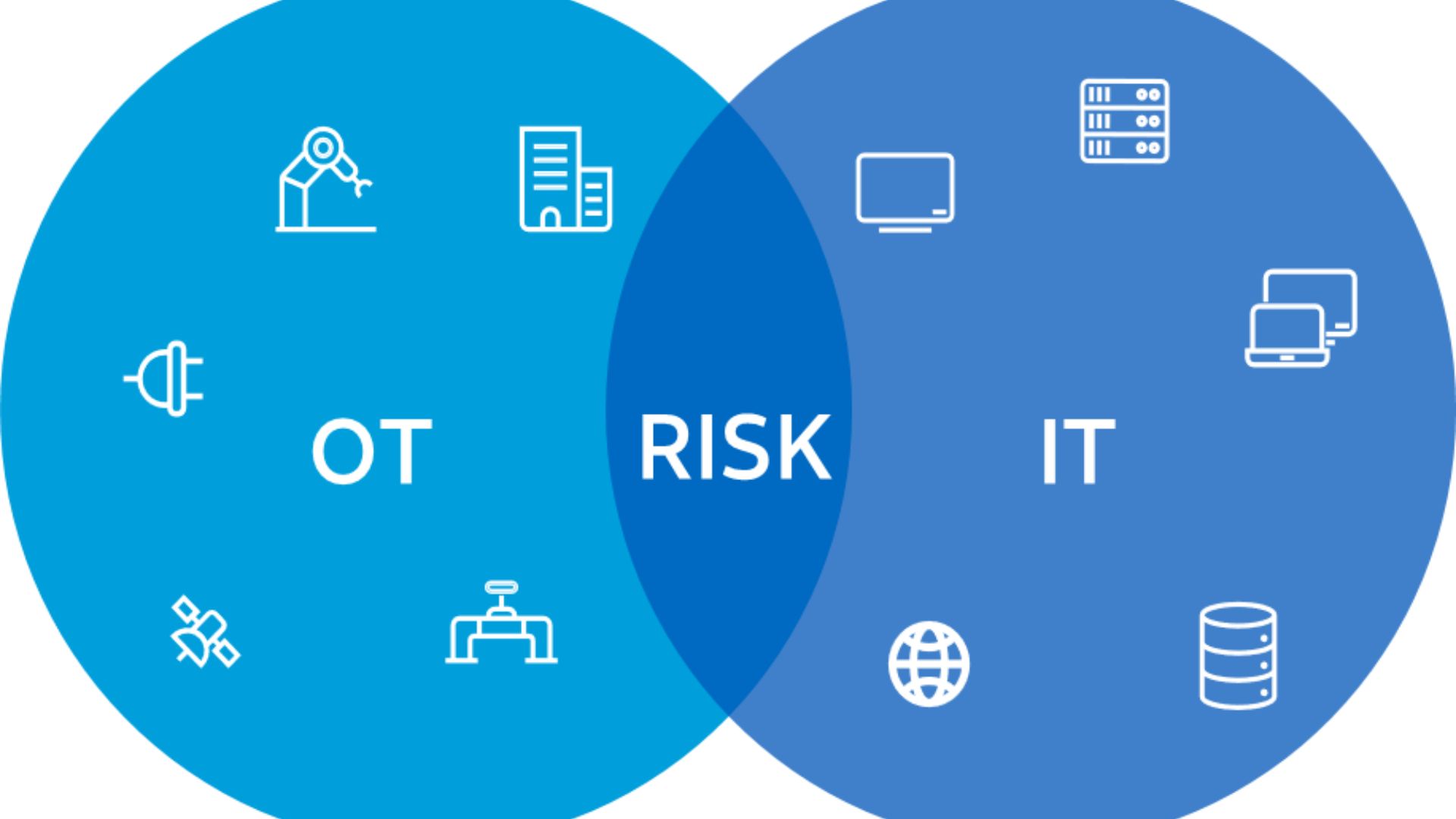
IT/OT network owners must protect Operational Technology (OT) systems in the continually changing cyber world. The main question is, How do IT/OT network owners keep these OT systems patched so the devices are less vulnerable?
Answering this question requires a proactive approach like an attacker. OT asset vulnerabilities are routinely published by the National Vulnerability Database (NVD) upon patch releases, making the vulnerability window critical. OT integration with the cyber-physical world increases hazards, with critical infrastructure cyberattacks rising sharply.
This article discusses patch management in operational technology environments, including proprietary protocols, regulatory constraints, and the need for thorough testing. It emphasizes the importance of staying ahead of potential adversaries to strengthen OT system security.
The OT Patch Management Process
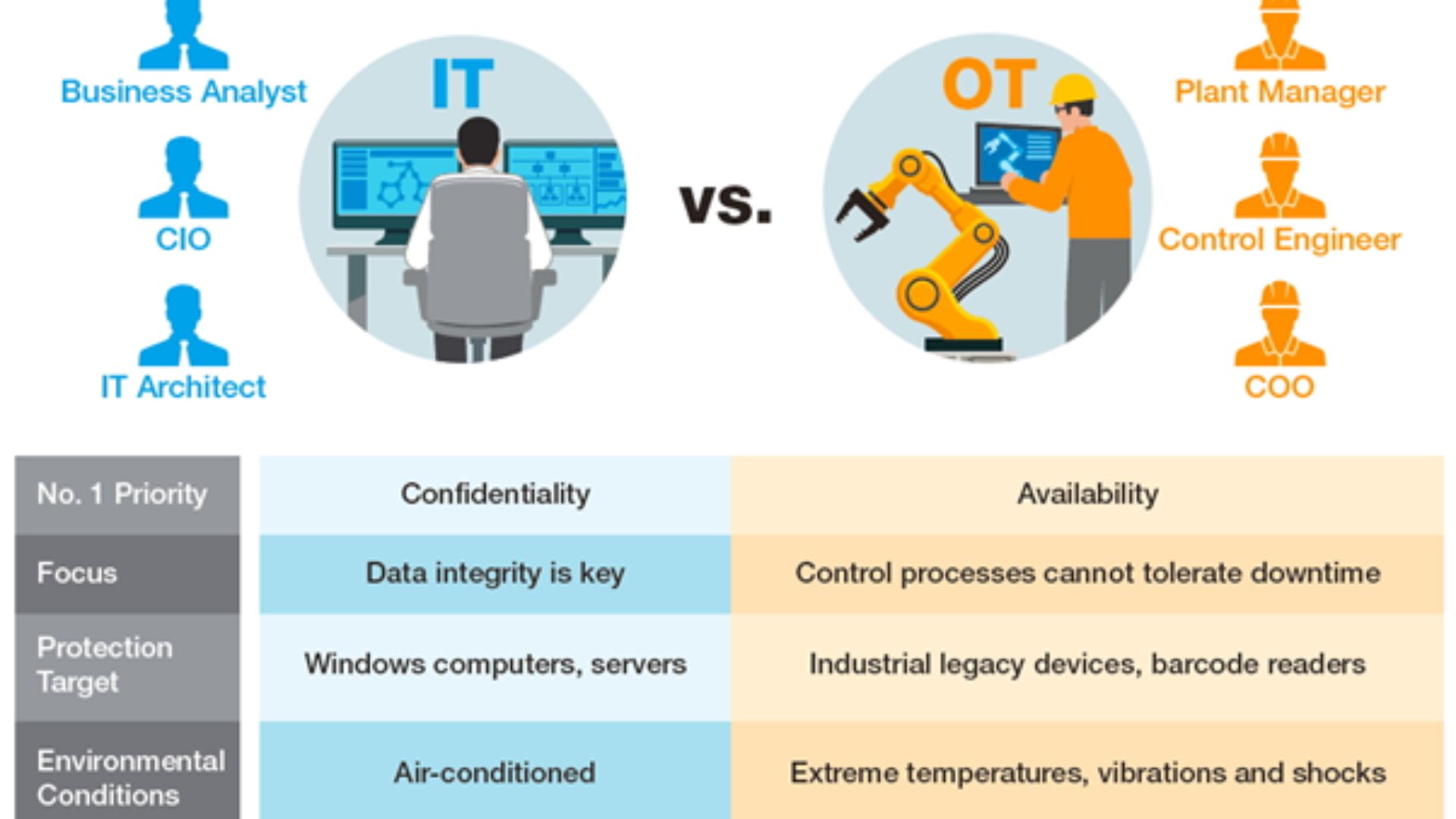
Usually, IT and OT critical infrastructure systems use different technology stacks and work on their own. These systems aren't directly linked to each other, so their controls are different from those on a computer network. They are also often on separate networks so that cyber risks like malware and ransomware threats don't overlap.
Evil people may be interested in an OT asset that is vulnerable because it can be an excellent way to make money. The National Vulnerability Database will find the flaws once the patch is made available to everyone. Hackers also keep an eye on these files all the time.
With ICS-CERT's security updates, you can be notified as soon as ICS-CERT finds a vulnerability. In just one weekend, NVD put out almost 350 samples. These flaws can hurt an OT group in a lot of different ways.
Why Cyber Risk To OT Systems Is Increasing
For a long time, industrial systems didn't have direct connections to the Internet and depended on their proprietary protocols and software. They were also controlled and watched over by people.
At that time, getting direct access to a terminal was the only way to get into OT systems, which was challenging. OT and IT (Information Technology) only worked together a little and had the same security holes.
Today, the story is very different. As part of efforts to go digital, the coming together of IT and OT is speeding up. More and more manufacturing systems are going online to share big data and intelligent analytics, as well as to get new features and work more efficiently by combining different types of technology.
As systems move from closed to open, a lot of new security risks appear. Threat actors are actively going after these, and they often succeed. This needs to be fixed. Also, a lot of the OT infrastructure is made up of specialized hardware and software that might have yet to be designed with hacking in mind.
In OT settings, there may be a lot of non-traditional destinations, like the Internet of Things (IoT) and industrial IoT. At times, these devices need an operating system that works or enough computing power to run security software like antivirus and anti-malware.
Industrial systems are more likely to be hacked as they become more linked together. Include old equipment, safety rules that say changes can't be made to the equipment, and compliance rules that say private data has to be shared with outsiders. This makes it hard to meet both the goals of business uptime and IT security.
Top 7 OT Patch Management Best Practices
There are a lot of different methods that people who own OT assets have to work with. It's even harder to do the job when different vendors' Industrial Control Systems (ICS) are installed in the OT setting.
These include DCS, SIS, PLC, and more. Because of this, it is essential to have a sound patch management system in place to find vulnerabilities and lower the risk to a reasonable level before attackers do. The next part will talk about the seven best ways to make the patch management process go smoothly.
Maintain A Comprehensive And Evergreen Inventory
An essential part of any OT patch management process is keeping a complete inventory of all the software, firmware, and hardware in the OT environment. This includes all the assets from the industrial demilitarized zone (level 3.5) to the cell/area zone (level 2-0) in the ISA/IEC-62443 Purdue model.
It will be easier to quickly find which patches are essential for the OT setting once there is a clear picture of what is there and how it works, along with the known vulnerabilities.
Assign Criticality To The OT Asset
To rate how vital the OT asset is, a method for rating how important it is must be set up. Because the safety system is regulated, this may already be the case. When figuring out how important something is, you need to think about how it will affect the business. For example, how losing accessibility, dependability, integrity, etc., will affect the safety, profits, etc., of the business.
For instance, the cost of a workstation that is used to set up and keep an eye on a safety system shouldn't affect how vital the task is. It would cost less than $1,000 for that desk, but if you can't get to, watch over, or change the safety system, something terrible could happen that would cost millions of dollars.
Seek New Patches And OT Vulnerabilities
The people who own OT assets should be on the lookout for new patches and holes. The company can sign up to be notified when each ICS provider releases patches. It can take a lot of work to keep track of patch release alerts from different vendors. If you sign up for the US-CERT/ICS-CERT vulnerability announcement, you will be the first to know about newly discovered flaws.
Prioritize Deployment Of Patches
It is not possible to work on all OT files at the same time with all patches. It's also not possible to patch each one separately. Patch deployment that is made explicitly for the OT setting should be given top priority.
A lot of different things are used to figure out the CVSS score, like the access vector, the difficulty of the access, authentication, integrity, availability, and so on. To figure out what to change, this is an excellent place to start.
Suppose there is a critical vulnerability (CVSS score of more than 9.0) on the training (low critical) asset and a high vulnerability (CVSS score between 7.0 and 8.9) on the critical safety system that is monitoring poisonous gas.
In that case, the high vulnerability should be fixed first, even if the CVSS score is lower. This is because exploiting that vulnerability will cost the organization more because it will directly affect people, the environment, and the plant.
Assess And Reduce Risk For Exempted Patches
In IT, all of the Windows operating system (OS) patches can be installed. In OT, however, installing all of the OS patches can cause a vital server or workstation to crash. This will directly affect how the plant works because critical assets will no longer be able to be accessed or watched. Because of this, OT groups must test the MS patches allowed by the ICS vendor on a non-critical testing environment before they are applied to production computers.
Patch As Part Of The Change Management Process
Standards in your field, like IEC-62443, say that you should have a method for managing change. Having a baseline, record, review, write, and rollback plan is a good idea for this process. It is important to remember that putting patches in the OT environment is a change to the environment, so the same change management method should be used.
Create A Patch Management Policy
For the organization to grow, it needs to have a written policy that all workers must follow, and that is updated as needed. A clear patch management policy and method are some of the best ways to be sure that patch management works well. Staff can follow the proper OT patch management process with the help of a patch management strategy.
Standards like IEC-62443 are already out there, so you don't have to come up with your process from scratch. The 2015 version of ANSI/ISA-TR62443-2-3-2015, which is about fix management in the IACS environment, is a great place to start creating a structured fix process.
Effects Of Cyberattacks On OT Environments
Because they can cause real problems like shutdowns, outages, leaks, and explosions, OT cyberattacks tend to be worse and have more significant effects than IT ones. There were 64 OT cyberattacks reported to the public in 2021, which is 140% more than the number reported in 2020.
About 35% of these had physical effects, and each one was believed to have caused $140 million in damage. (Source: MCkinsey)
Ransomware incidents rose by 87% in 2022 because of geopolitical risks. Europe and North America saw the biggest jumps, with 40% more incidents in North America, 32% more incidents in Europe, and 28% more incidents on other continents compared to 2021 data.
Cyberattackers often take over OT devices by using ransomware and third-party links that aren't as safe. This can stop operations and production. When trying to protect themselves from these kinds of attacks, industrial organizations often have to deal with technical and practical problems like the ones below:
- Legacy systems, which can be 30 years old or older, have old security holes and few security controls. For example, attackers can use a specially-made font to run malicious code on 2008 Windows computers.
- It's hard to put security controls on OT devices that were made before cybersecurity became a problem and are handled by OEMs. For example, sensors that were put on valves and linked to a network without going through internal hardening procedures.
- Third-party remote links control OT devices that are linked to an internal network (for example, hackers can get into a network set up by a vendor and use it to infect other devices).
- It's easier to centralize, control, and police OT cyber operations when there is clear ownership between the OT and IT teams. For example, it's easier to connect manufacturing execution systems with enterprise resource planning by setting up a 3.5 demilitarized zone.
- There are different levels of risk tolerance, which means that OT decision-makers have to choose between increasing output and keeping devices safe. For example, they have to choose between increasing production and patch management, which could stop operations.
- Not enough people with the right mix of cybersecurity and automation skills and experience with cybersecurity and automation control systems (for example, an expert in OT cybersecurity but not enough automation and process knowledge).
- Because of business, operational, and technical limitations, a continuous process may run for three years before it is scheduled to stop. This makes it harder for OT teams to fix devices and put in place time-sensitive solutions, like turning off the power to a working server so that it can get a security patch.
Four OT Patching Hurdles To Overcome
OT/ICS systems that need to be patched come with several significant problems. Some of these problems are:
- Patching Constraints- Patching is only sometimes allowed in OT/ICS settings because it costs money to have the system down. In way too many workplaces and other OT settings, the times when patching is allowed are too far apart.
- Legacy Systems- Proprietary Protocol Complexities. It's been decades since these OT/ICS gadgets have been used in these places. A few decades ago, designing a safe environment was only sometimes a top priority. The air gaps that were put in place have long since been removed as these systems became more interconnected.
- Vulnerability Assessment Woes - Most of the time, traditional vulnerability scanning tools don't work well in OT/ICS settings and can cause a lot of problems. This makes it hard to find systems that need to be updated or make sure they have been fixed.
- Diversity Of Systems- There are a lot of different systems used in OT settings, and it's even harder to keep track of them all when OT/ICS devices come from different manufacturers. This means that effective patch management is needed to find holes and lower the risk to a safe level.
The Future Of OT Security
Because automation technology is being used more and more in the utility business, it is essential to protect operational technology (OT) systems from cyber threats. As of 2023, there are more and more advanced cyberattacks on utilities that can stop them from doing their jobs, cost them money, and even put people's safety at risk.
In March 2021, the group DarkSide used ransomware to attack the Colonial Pipeline, which moves a lot of fuel from Texas to the eastern US. The attack led to the company's data being encrypted and a demand for a fee. When fuel sources were cut off, people rushed to gas stations in the affected areas to buy fuel.
The fact that Colonial Pipeline paid the ransom to end the attack showed how badly cyberattacks can damage critical infrastructure like utility businesses. The North American Electric Reliability Corporation (NERC) has guidelines for Critical Infrastructure Protection (CIP) that utilities must follow to protect their systems from these threats.
These guidelines, which all utilities regulated by NERC must follow, spell out specific ways to keep OT systems and data safe, which are necessary for the bulk power system to work reliably. Vital cybersecurity means must be put in place to stop people from getting into OT systems without permission as part of NERC CIP compliance.
Some of the things that fall under this category are network segmentation, access controls, and incident reaction plans. Also, utilities need to check and test their OT security controls daily to make sure they work.
The NERC CIP framework includes a guideline called CIP-010-4, which spells out how to keep critical cyber assets safe. These are things like computer systems, data, and communication tools that could be lost, hacked, or used in a way that would seriously damage the bulk power system's ability to work reliably.
Frequently Asked Questions
What Is OT Patching?
Operational Technology (OT) Patching involves updating and securing software in industrial control systems and critical infrastructure.
What Is A Patched Operating System?
A patched operating system has the latest updates and security fixes applied to address vulnerabilities and improve system stability.
How Do You Patch Systems?
Patching systems involves applying software updates, including security patches and bug fixes, to keep software and operating systems secure and up-to-date.
What Is A Patch Management System?
A patch management system is a tool or process for efficiently deploying, monitoring, and managing software patches across an organization's IT infrastructure.
Conclusion
Protecting Operational Technology (OT) systems from new cyber dangers is a difficult job that needs close attention from people who own both IT and OT networks. The coming together of IT and OT, which is made possible by digitizing industrial processes, brings both good and bad things.
A strong patch management plan is needed to answer the critical question, "How do IT/OT network owners keep these OT systems patched so the devices are less vulnerable?" It is essential to follow best practices like keeping an accurate inventory, figuring out which assets are the most important, keeping an eye out for new patches, putting deployments in order of risk, and including fixing in the change management process.
As IT and OT become more connected, it's important to take effective steps to reduce cyber risks and make sure that critical infrastructure systems can handle a threat in an environment that is always changing.