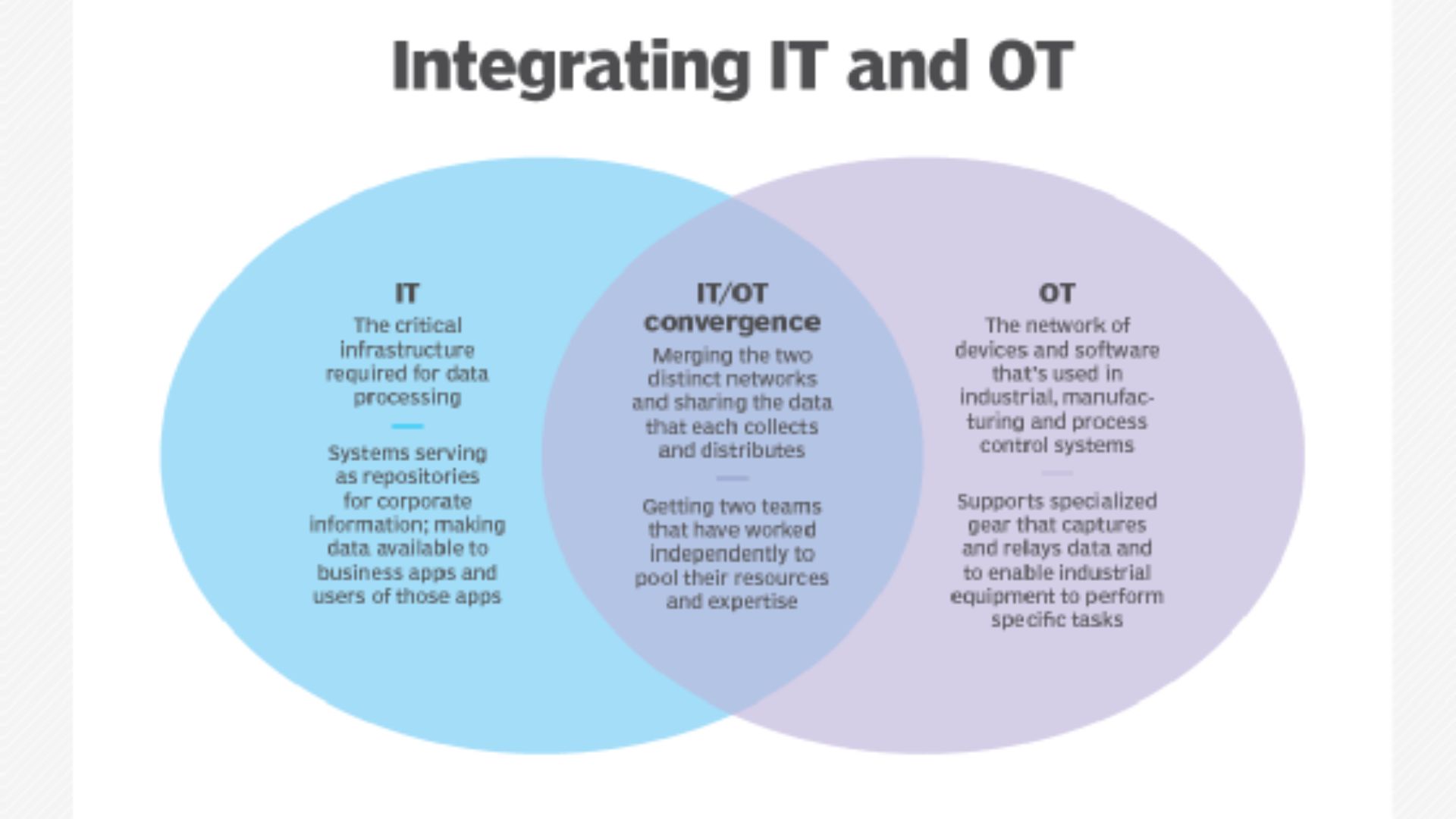
Integrating IT and OT is essential for holistic security and risk management for mining and metals industries, as well as any company that generates most of its income and has considerable OT risk. Wanting it done won't get it done because this is a people and trust issue, not a technical issue.
Be a process and site learner before making substantial technical and process improvements to develop trust and connections. You need a license to advance technical and security goals. This license must be obtained via trust, not from top leadership. In this article, we will be discussing what are effective compensating controls in IT/OT environments.
What Is Compensating Control?
A compensating control, also known as an alternative control, is used to meet a security standard that is too difficult or impractical to execute. In December 2004, the PCI Security Standards Council (PCI SSC) added compensating measures in PCI DSS 1.0.
Since then, the PCI SSC has updated the standard regularly. The most recent version, 4.0, was released in March 2022. Between 1.0 and 4.0, compensating control information changed slightly, but the guidelines remained consistent.
The PCI SSC proposes compensating controls for security criteria that cannot be satisfied "due to legitimate and documented technical or business constraints." Compensating controls must reduce the original requirement risk. The PCI DSS requires compensating controls to do this.
- Maintain the original requirement's meaning and standards.
- Provide a similar defense to the original PCI DSS requirement so that the compensating control compensates the risk it was designed to defend against.
- Go "above and beyond" PCI DSS requirements (compliance is not a compensatory control).
- Address the higher risk of not following PCI DSS.
- Current and future requirements must be met; a compensating control cannot fix past requirements.
Why Integrate IT And OT Security?
Even with firms that generate most of their revenue and risk from operational technology, cyber security teams typically focus on IT networks and ignore OT. Previously, this technique made sense. Early OT networks used obscure, proprietary, and highly customized networks and technologies.
IT technologies, including Windows, Linux, IP networks, virtualization, and the cloud, underpin current OT networks. With the commoditization of OT, IT cyber attacks are causing more OT repercussions in critical infrastructure and other OT domains. Breaking silos to expand IT security to OT networks has essential strategic and tactical benefits. This includes:
Streamlining Of Detection And Response
Over 91% of OT attacks start in IT via phishing emails or other means. IT and OT security integration tracks attacks across both domains. Unifying detection and response across domains will reduce the business effect by speeding up threat detection, response, and remediation. (Source: yeoandyeo)
Make The Best Use Of Limited Human Resources
Integrating IT and OT security optimizes your security staff. In isolated rural locations where mining activities are located, recruiting and retaining skilled security teams takes a lot of work. Expanding your IT staff into OT allows for growth, learning, and concentration on the company's most significant risks. This helps retain security personnel in your firm.
Optimize Investment In Security Tools
Investment in tools spanning IT and OT security is possible with integration. The operation will be more efficient and can tackle operational problems with security toolsets if planned well.
Simplified, Centralized Risk Management
OT risk management is complex, although most mines and plants have mature risk management processes. Security integration into OT lets you show and integrate OT security concerns into plant and business risk management systems.
Centralizing risk (or communicating risk in the exact words) will only improve company-wide cyber risk understanding and capital allocation decisions.
Effective OT Compensating Controls To Consider
Experts advise the following compensating controls:
- Accurate asset inventory - The complexity of OT/ICS environments, unique protocols, and aging legacy systems make accurate inventory difficult. Visibility into the environment allows accurate asset inventory and understanding of environmental relationships and dependencies. This enables more thorough security measures, especially for internet-facing devices and networks.
- Allow only approved devices and systems - Only certified devices and apps should run in the environment.
- System and network segmentation - Network segmentation can compensate for the inability to secure IT and OT networks equally. Segmentation separates a network into autonomous physical or virtual zones. Segmented networks can contain intrusions by isolating security issues to one network segment and reducing the likelihood of virus or attack proliferation.
- Strengthen access controls - Clearing devices of default passwords and mandating solid passwords and multi-factor authentication will improve environment security.
- Network monitoring- An asset inventory, recording known vulnerabilities, mapping vulnerabilities to assets, and closely monitoring activity can reduce risk, especially with an incident response strategy for suspicious activity. Increased monitoring and detection can compensate for weak preventive interventions.
Adequate IT Compensating Controls To Consider
Compensation controls compensate for an organization's core controls' inadequacies. IT environments need compensatory measures to stay strong and safe. Consider these adequate compensatory controls:
- Multi-Factor Authentication (MFA)- MFA adds protection beyond passwords, reducing unwanted access.
- Network Segmentation- Segment the network to restrict attackers' lateral mobility. This reduces security breach damage.
- Intrusion Detection and Prevention Systems (IDPS)- IDPS can automatically respond or alert for malicious network and system activity or security policy violations.
- Data Encryption- Encrypt sensitive data in transit and at rest to prevent unauthorized access even if perimeter protections fail.
- Regular Security Audits and Penetration Testing - Perform regular security audits and penetration tests to find IT infrastructure issues. Resolve concerns quickly.
- Security Information and Event Management (SIEM)- Collect, analyze, and correlate log data from multiple sources with SIEM solutions to discover security events early.
- Endpoint Protection - Implement robust endpoint protection solutions with antivirus, anti-malware, and EDR.
- Security Awareness Training - Regularly train staff on security best practices, including phishing, social engineering, and other cyber risks.
- Incident Response Plan- To respond quickly and effectively to security issues, create and test an incident response strategy.
- Backup and Disaster Recovery- Backup vital data and create a disaster recovery plan to maintain company continuity in the event of data loss or system failure.
IT/OT Convergence Benefits
Converging IT and OT can help utilities despite these hurdles. IT/OT convergence simplifies complicated system data analysis, monitoring, and control. Because workers can analyze data from anywhere, they can work more effectively and make better decisions. Converged data gives leaders and employees real-time insights. IT/OT convergence has further benefits.
- Less siloed departments- As IT and OT share expertise and handle convergent technologies, segregated departments will merge.
- Digitized maintenance process - After IT/OT convergence, teams can foresee device failures and optimize resource consumption. Digitized maintenance allows utilities to scale their systems to accommodate additional digital devices. IT/OT convergence lets utilities analyze device data directly, improving system security.
- Improved cybersecurity - Any company needs cybersecurity to secure customer data and IP. Linking machines has benefits, but the transformation and increased cybersecurity threats require a new cybersecurity strategy.
- Less unexpected downtime- IT/OT convergence reduces unexpected downtime. Unlike preventive maintenance, predictive maintenance solutions allow firms to monitor for equipment failures, collect real-time data from affected assets, and repair during scheduled downtime. Thus, utilities can extend asset life and drastically cut repair expenses.
- More efficient resource and energy use - IT/OT convergence can improve workforce and energy efficiency as an OT system becomes more active and aligned with a utility's goals.
- Better management, auditing, and visibility - Utility management, auditing, and visibility can improve with IT/OT convergence.
- Improved efficiency for asset management- The integrated administration of OT and IT systems makes IT/OT convergence more efficient for asset management.
- Better compliance with regulatory standards- Integrating IT and OT improves administration, auditing, and visibility, helping utilities meet regulatory requirements. Safe and profitable operation requires this.
- Improved visibility and automation for distributed OT- Utility visibility and automation for remote OT can improve as the OT department transmits maintenance data in real time.
- Reduced costs for operations, support, and development - With IT/OT convergence, utilities may cut operations, support, and development expenses. Substantial cost reductions can result.
Challenges To Effective IT/OT Convergence
IT/OT convergence has several benefits, and many firms want a smooth connection. What are the obstacles? Each manufacturer has distinct digitalization issues depending on its business processes. However, most manufacturers face these issues:
- Siloed processes and expertise- To integrate IT and OT personnel, processes, and systems, it may take time to tear down old walls.
- IoT security - Integration with IT increases the OT attack surface because IoT devices have been exposed to attacks. The firm should prioritize cybersecurity because OT ensures smooth facility operations.
- Integrating the tech stack - Programming languages, gateways, and platforms vary in IT and OT systems. The firm may need to integrate IT/OT manually to achieve smooth convergence.
How Can We Overcome Challenges And Seize Opportunities With IT/OT Convergence?
IT/OT convergence is the future, but it must be planned and executed. Business leaders must create a strategy-aligned roadmap to connect IT and OT systems. To maximize performance, company executives must maintain organization-wide alignment, as with any change management.
To prepare employees for continuous development across the organization and give them the tools they need to succeed in today's digital-first environment, upskilling and reskilling must continue. INCIT supports manufacturers who are integrating IT and OT to establish dynamic, adaptable, and future-ready organizations by providing the tools and reach.
Frequently Asked Questions
What Are The Common Challenges In OT Security Explain?
Many OT environments rely on outdated and unpatched systems.
What Are The Challenges Of IT And OT Networks?
Merging IT and OT networks introduces compatibility and security challenges.
What Are The Significant Challenges In Information Security?
Evolving and sophisticated cyber threats pose constant challenges.
Why Is Securing ICS OT Environments A Challenge?
Patching and updating systems in OT often pose operational risks.
Final Thoughts
Businesses are transformed by IT-OT integration. It improves monitoring, reaction, and resource use. Businesses must implement strong compensating controls to manage IT and OT mergers.
Compensating controls reduce IT and OT risks by managing legacy systems, network segmentation, and access controls. A thorough OT strategy contains a list of assets, device restrictions, and solid network tracking. Multi-factor authentication, encryption, and security audits are crucial in IT.
Businesses must plan, have a complete plan, ready workers, and aligned goals to solve difficulties. Good compensating controls in IT/OT contexts strengthen and prepare organizations for technology changes. What Are Effective Compensating Controls In IT/OT Environments? This question emphasizes the need for proactive convergence trip security.